Manage Entra Privileged Identity Management with Terraform - Part 2: Entra Groups
In THIS previous post we looked at managing Entra Privileged Identity Management (PIM) with Terraform and working with Azure RBAC roles. That is great but did you know that you can onboard Entra Groups to PIM and therefor also manage them in Terraform?
In todays post we'll look into some base code for managing this, expanding on what we already know about managing PIM and RBAC roles via Terraform.
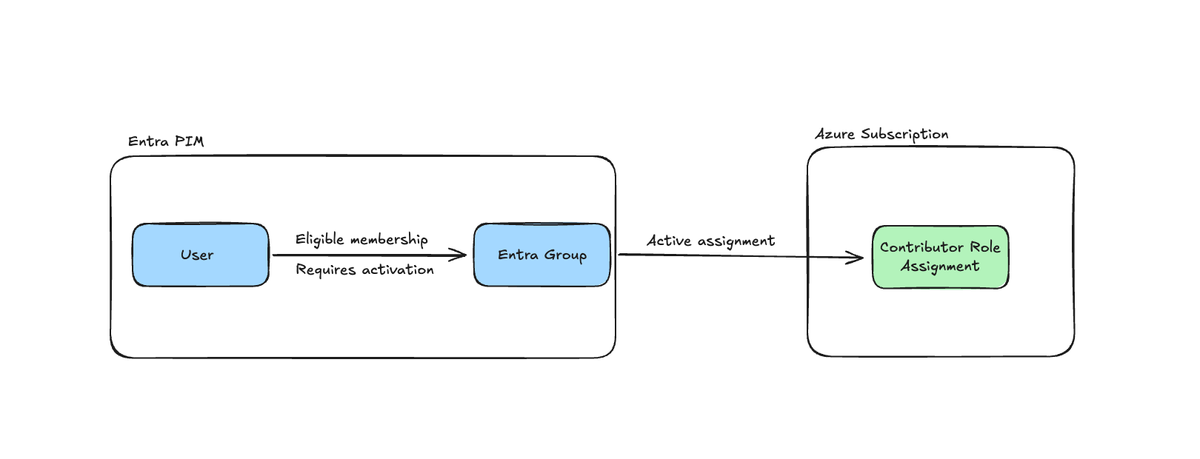
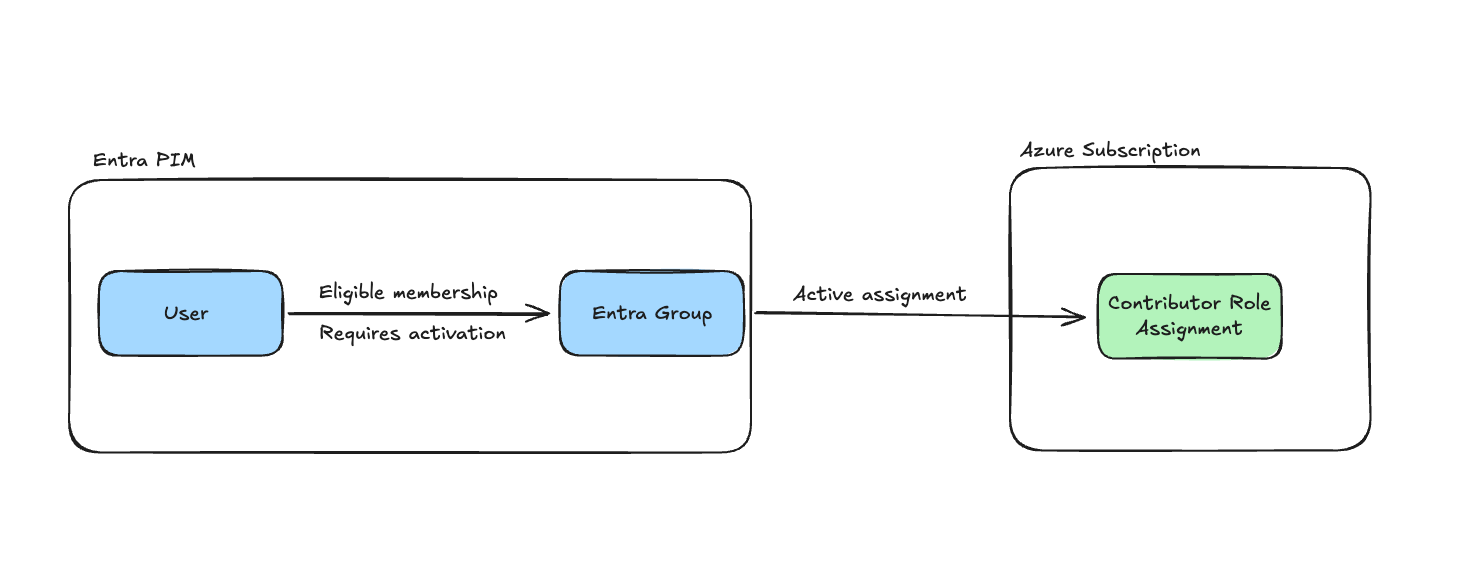
This is what we will configure in this post:
Setup the code
We'll start by getting some base code confguration setup in our main.tf file.
terraform {
required_providers {
azurerm = {
source = "hashicorp/azurerm"
version = "4.8.0"
}
azuread = {
source = "hashicorp/azuread"
version = "3.0.2"
}
}
}
provider "azurerm" {
features {}
subscription_id = var.subscription_id
}
data "azuread_client_config" "current" {}
resource "azuread_group" "this" {
display_name = "ad-${var.environment}-admins"
owners = [data.azuread_client_config.current.object_id]
security_enabled = true
}We are as you can see also creating an Entra Group which will be the one that we will assign a permanent assignment to an Azure RBAC role. Members of this group will however only be eligible members.
Next we will make use of a key resource which is azuread_group_role_management_policy where we will onboard the group to PIM and configure important settings like activation rules, eligible assignment rules and notification rules.
This is what my resource looks like:
resource "azuread_group_role_management_policy" "this" {
group_id = azuread_group.this.object_id
role_id = "member"
activation_rules {
maximum_duration = "PT9H"
require_justification = true
approval_stage {
primary_approver {
type = "groupMembers"
object_id = azuread_group.this.object_id
}
}
require_approval = true
}
notification_rules {
eligible_activations {
approver_notifications {
default_recipients = true
notification_level = "Critical"
}
}
}
}- We target the AD group we created earlier
- Role is can be either
memberorowner - Max duration the active membership in the group will be active for is 9 hours
- We require approval and approvers is members of the group itself. This means any other user can approve the request but you cannot approve your own request
Next we need to actually apply this configuration to the PIM onboarded group which we do with a resource called azuread_privileged_access_group_eligibility_schedule
resource "azuread_privileged_access_group_eligibility_schedule" "this" {
group_id = azuread_group_role_management_policy.this.group_id
principal_id = azuread_group.this.object_id
assignment_type = "member"
permanent_assignment = true
}Role assignment
Finally we need to setup the active role assignment of the group to the Contributor role. This means that users who are eligible to assign themselves active member of the group will in turn get access to the Contributor role of the subscription where the group is assigned:
data "azurerm_role_definition" "contributor" {
name = "Contributor"
}
resource "azurerm_role_assignment" "contributor" {
scope = "/subscriptions/${var.subscription_id}"
role_definition_id = data.azurerm_role_definition.contributor.id
principal_id = azuread_group_role_management_policy.this.group_id
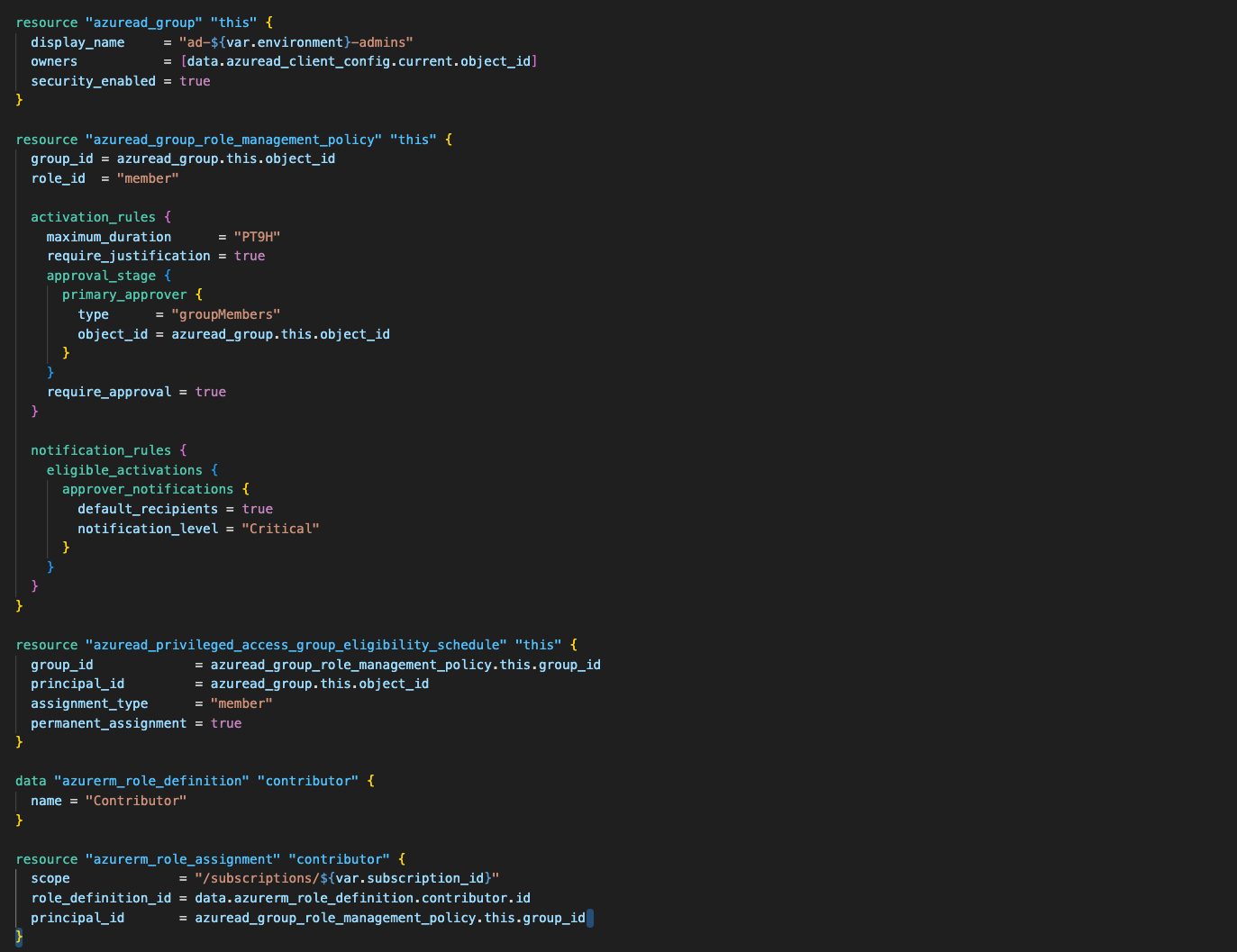
}This is what the code looks like now:
Conclusion
With this post together with my previous post concludes this dive into Terraform and Azure PIM. You now have a starting point for setting up both direct role assignments to Azure RBAC roles with PIM or use groups. There are benefits to using both depending on your requirements.
You can find the complete code inside the Github Repo for this post which you can find HERE
References
About me



