List policy exemptions in Azure with Resource Graph
Sometimes we exempt things
In Azure we often use Azure Policy as a tool to govern our cloud environment. This can be anything from enforcing certain locations being used (Or rather disallowing certain locations), restrict which resources can be configured and all the way down to specific settings on Azure resources.
This is done with the intent of making our environment secure. However, I think anyone that has worked in Azure has found that all the guardrails that can be enforced are not always possible. Sometimes there may be restrictions in applications and systems that will not work with all the hardening in place.
This is where some would say "Well in that case the application is not going up, it's not secure". However, I have found that whilst this is what we strive towards this is not always the reality. Sometimes I may not even agree with some of the restrictions that the guardrails put in place. Anyways, we end up in a situation where we and the stakeholders agree that we will exempt this lock down for this application.
So we exempt things
And then what? Just because we allow this exemption due to a waiver in the policy, that does not automatically mean that we should allow this exemption forever. Now, there is a way when you create the exemption that you can set it to expire, however, I usually forget. We are humans and we cannot rely on ourselves to always remember and follow these expirations.
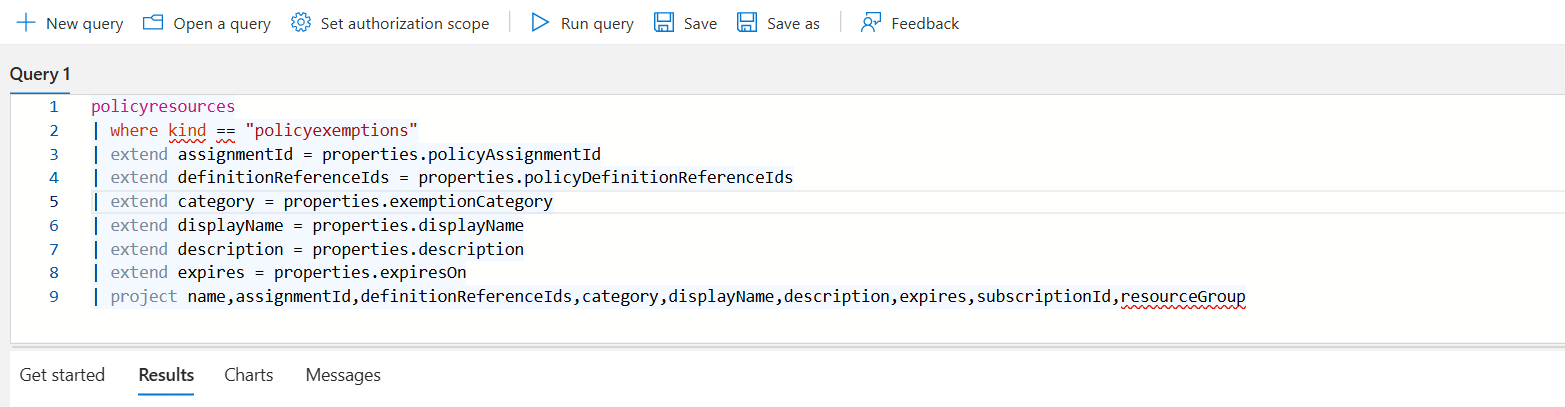
Luckily for us we can use a great tool called Azure Resource Graph. This lets us query almost all things in Azure and now we can query and list exemptions. I've written an example query which takes all resources of the type policyExemptions and manipulated the result to remove some of the fluff:
policyresources
| where kind == "policyexemptions"
| extend assignmentId = properties.policyAssignmentId
| extend definitionReferenceIds = properties.policyDefinitionReferenceIds
| extend category = properties.exemptionCategory
| extend displayName = properties.displayName
| extend description = properties.description
| extend expires = properties.expiresOn
| project name,assignmentId,definitionReferenceIds,category,displayName,description,expires,subscriptionId,resourceGroupThis should give you a comprehensive list of policy exemptions in your environment. You can take this and:
- Export to CSV and send to decision makers
- Schedule to run once per month (or at whatever frequency you like)
Etc etc. That's it! Hope you like it and be sure to checkout my video I made where we delve into some more ARG queries and just have a general good time:
About me

