Azure Firewall
Azure Firewall is a firewall service in Azure that can do several things for you. It can inspect traffic flowing in and out of your environment, it can scale automatically depending on the load of traffic you experience and much more. It works with availability zones in your Azure Environment. Simply a fully managed service which is stateful.
What does Stateful mean?
A stateful firewall is a firewall that can monitor and keep track of communications inside your network in addition to blocking incoming & leaving traffic.
It gives you more information as it will monitor the entire connection, not just block traffic designated as dangerous once it arrives and leaves the network which a more basic firewall does. This is important because if you monitor the connection you can gain more information and insights into your networks traffic.
This information can be used to identify threats and patterns in your environment.
Difference between Azure Firewall and Azure Application Gateway & Azure Application Firewall
Azure Firewall operates at layer 3 & 4 of the OSI model which is TCP/UDP, IP, ICMP and so forth. If you are looking for more of Layer 7 which is application then Azure Application Gateway is the recommended option. An example of this type of inspection is looking at URLs end-users use and decide on actions based on this information.
Azure application gateway is often used in conjunction with web application firewall to protect yourself further from common exploits such as SQL-injection attacks or if you for example want to use geo-filtering.
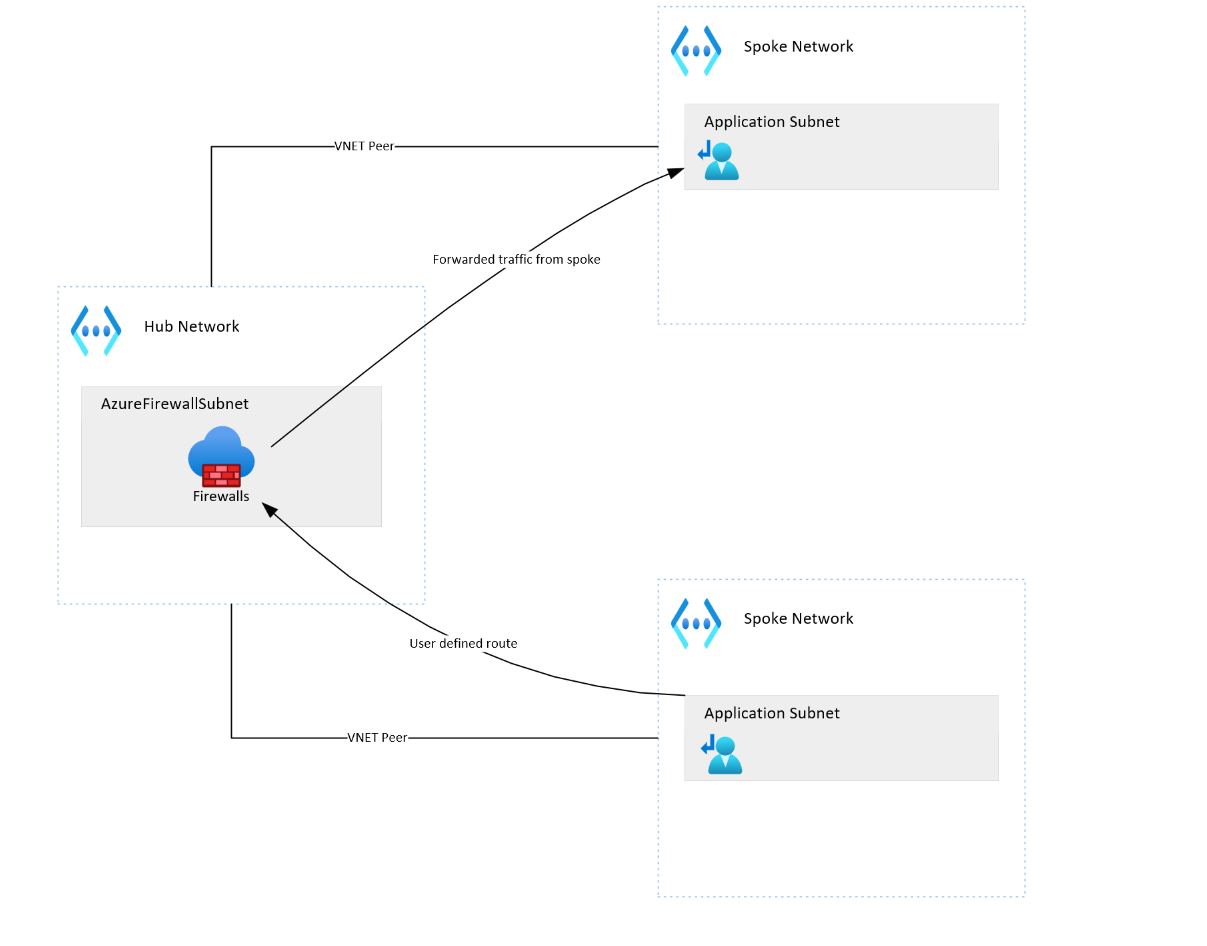
Azure Firewall enables spoke-to-spoke communication
In a hub-and-spoke network topology which is a classic one in Azure by default the spokes do not talk to eachother, they only talk to the hub.
With Azure Firewall you can enable spoke-to-spoke communication by using route tables on subnets in the spoke virtual network and route traffic to a VirtualAppliance as next-hop, which in this case will be the internal IP of the Azure Firewall.
If you have configured your peering to allow forwarded traffic the Azure firewall can then send this traffic from one spoke to another, enabling resources to talk to eachother.
Restrictions
Some limitations that are good to know when it comes to Azure Firewall
- The Azure Firewall must be placed in the same resource group as the Virtual Network it is registered to.
- There can only be one Azure Firewall per Virtual Network.
- Azure Firewall requires a /26 subnet
Controlling costs in lab environments
Azure Firewall can be very costly. Often this is not a problem for enterprises but if you want to mess around with it in your own lab here is a tip:
You can turn the Azure Firewall appliance on and off using Azure Powershell. Just be cautioned that traffic that relies on the firewall appliance will stop working but in lab environments this can be okay.
Azure Firewall calculates it costs by data processed and running hours, if you turn it off in Powershell that amounts to 0.
# Stop an existing firewall
$azfw = Get-AzFirewall -Name "FW Name" -ResourceGroupName "RG Name"
$azfw.Deallocate()
Set-AzFirewall -AzureFirewall $azfw# Start the firewall
$azfw = Get-AzFirewall -Name "FW Name" -ResourceGroupName "RG Name"
$vnet = Get-AzVirtualNetwork -ResourceGroupName "RG Name" -Name "VNet Name"
$publicip1 = Get-AzPublicIpAddress -Name "Public IP1 Name" -ResourceGroupName "RG Name"
$publicip2 = Get-AzPublicIpAddress -Name "Public IP2 Name" -ResourceGroupName "RG Name"
$azfw.Allocate($vnet,@($publicip1,$publicip2))
Set-AzFirewall -AzureFirewall $azfwIf the firewall is configured to use forced tunneling stopping is the same but to start run this snippet:
# Start the firewall
$azfw = Get-AzFirewall -Name "FW Name" -ResourceGroupName "RG Name"
$vnet = Get-AzVirtualNetwork -ResourceGroupName "RG Name" -Name "VNet Name"
$pip= Get-AzPublicIpAddress -ResourceGroupName "RG Name" -Name "azfwpublicip"
$mgmtPip2 = Get-AzPublicIpAddress -ResourceGroupName "RG Name" -Name "mgmtpip"
$azfw.Allocate($vnet, $pip, $mgmtPip2)
$azfw | Set-AzFirewallConclusion
Azure Firewall is a powerful solution that is a cornerstone service in many environments. We have only covered some of its features in this post, in future blogposts I will explore more of the Azure Firewalls capabilities.
Thank you for reading!
References
John Savills video on Azure Firewall

About me
